Researchers at cybersecurity firm Kaspersky Lab say that ASUS, one of the world’s largest computer makers, was used to unwittingly install a malicious backdoor on thousands of its customers’ computers last year after attackers compromised a server for the company’s live software update tool. The malicious file was signed with legitimate ASUS digital certificates to make it appear to be an authentic software update from the company, Kaspersky Lab says.
ASUS Live Update is an utility that is pre-installed on most ASUS computers and is used to automatically update certain components such as BIOS, UEFI, drivers and applications. According to Gartner, ASUS is the world’s 5th-largest PC vendor by 2017 unit sales. This makes it an extremely attractive target for APT groups that might want to take advantage of their userbase.
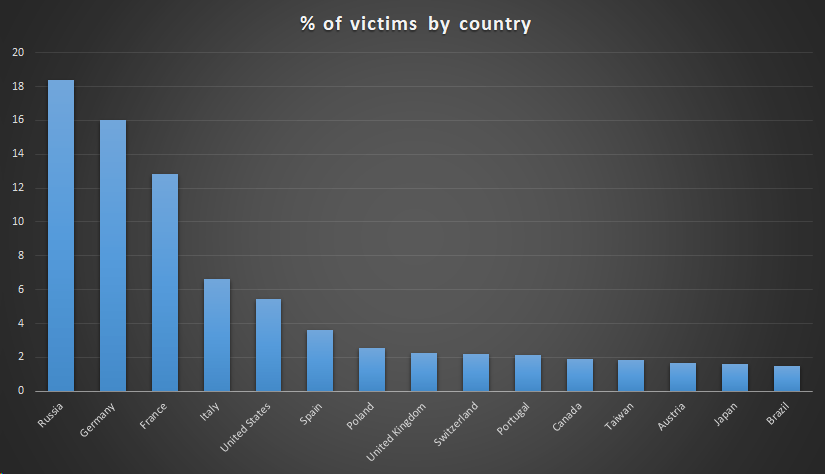
In below you can see percentage of the victims by counries.
With access to the update server, the attackers were able to distribute malicious files that appeared legitimate because they were given an ASUS digital certificate to make them appear to be authentic. Instead, the phony software updates gave the attackers a backdoor to access infected devices. Kaspersky estimates that about half a million Windows machines received the backdoor from ASUS’ update server. However, the attackers appear to have only been targeting about 600 systems. The malware was designed to search for machines by their MAC address. It’s not clear for what reason that the attackers focused on that small subset of machines.
The targetted supply chain attack on ASUS software update utility was initially discovered In January 2019, and the attack appears to be active since June to November 2018.
Check if your device has been targeted by the ShadowHammer cyberattack
If you have question about this or other our post, Contact US
